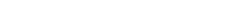525, Gangnam-daero, Seocho-gu, Seoul, Republic of Korea l Tel : 822-3448-0880 l Fax : 822-3448-0804 l Email : jsshim@truecut.co.kr
Copyright (C) 2015 TrueCut Security, Inc. All Right Reserved.
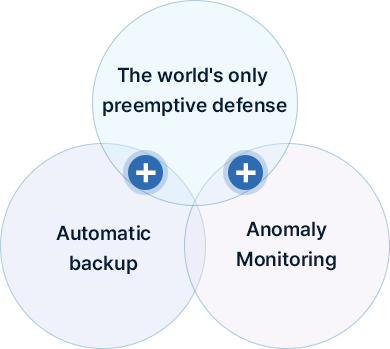
Solve all your IT concerns at once
All In One

- Absence of asset management for work PCs
- Control of non-business use of work PCs
- Absence of data management for retirees
- Absence of co-use PC management
- Absence of understanding network configuration

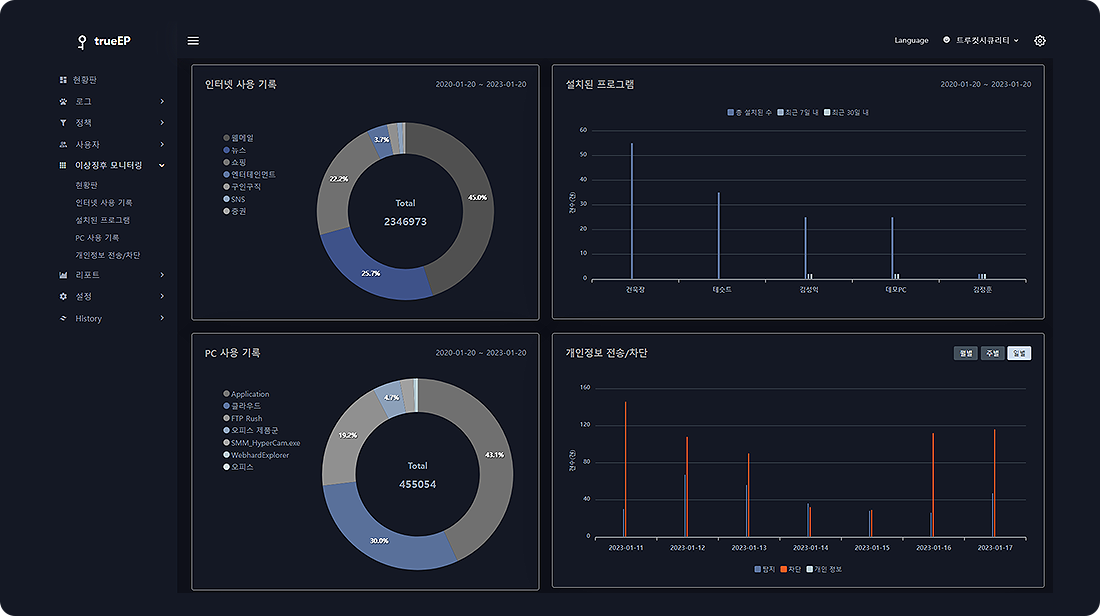
- Provides resource usage information of PCs
- Provides program information installed on PCs
- Provide resource usage information by program
- Provide PC usage record information
- Provide Internet usage history information
- Blocking Unauthorized Programs
- Full automatic backup
- Provides network information such as MAC, IP

- Hacking
- Data leakage by insiders
- Ransomware attacks
- Unknown zombie PCs
- Security incident follow-up
- Personal information security

- Prevent hacking attacks
- Logging insider's data transfer history
- Prevent ransomware attacks
- Block unknown excessive traffic
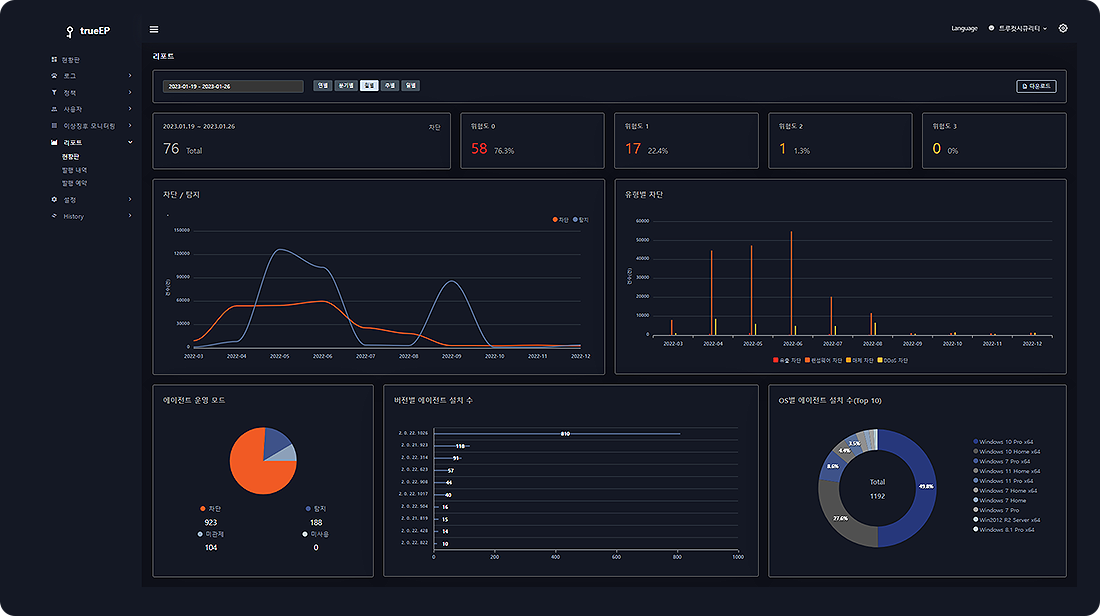
- Automated log analysis
- Tracing personal information files

- Hacking attacks
- Ransomware attacks
- Unknown upload to P2P
- Unknown zombie PC
- Too many security programs
- Deleted files by mistake

- Prevent hacking attacks
- Prevent ransomware attacks
- Prevent known upload to P2P
- Block unknown excessive traffic
- All in one seurity
- Full automatic smart backup
trueEP?
Anti-Hacking
- 1Data Hacking Prevention
- 2File Attachment Control
- 3Preventing Zombie PCs
- 4Media-Use Control
- 5Internet Access Control
- 6Anomaly Monitoring
Anti-Ransomware
- 1Ransomware Attack Prevention
- 2Fully Automatic Smart Backup
- 3Anomaly Monitoring
EPS
(Endpoint Protection System)
- Anti-Hacking
- Anti-Ransomware
- Anomaly Monitoring
Introduction of Anti-Hacking functions
| Div | Functions | Features of trueEP |
|---|---|---|
| Data Hacking Prevention | Data hacking prevention | Blocking exporting files stored on the disk without user input |
| Tracing personal information files | Notification of personal information document transmission | |
| Logging insider's data transfer history | Logging exporting files stored on the disk by insider | |
| File attachment control | Restrict transmission of files by attaching them to e-mail/messenger | |
| Restrict the size of files attached to e-mail and messenger | ||
| Print security | When printing, insert a watermark - image or text | |
| Logging printing history | ||
| Preventing Zombie PCs | Block unknown excessive traffic | Block when traffic above the threshold (adjustable) occurs without user input |
| Media-Use Control | USB-Media control | USB-Media set to Enable/Disable/Read only mode |
| Allow only authorized USBs to be used | ||
| Tethering control | Prevent tethering function from being used | |
| Blacklist control | Block the execution of programs by blacklist | |
| Internet access control | Block the access of internet by blacklist |
Introduction of Anti-Ransomware functions
| Div | Functions | Features of trueEP |
|---|---|---|
| Ransomware attacks prevention | Blocking ransomware behavior | The only product that can defend against unknown ransomware |
| Full automatic smart backup | Smart backup |
Run backup only during CPU idle time Stop backup while using PC Specify the storage space size according to the user's PC status Automatic deletion of old files when storage space is insufficient Set up only specified folders or files to be backed up |
| Full automatic backup |
Self-backup without user intervention Backup by automatically recognizing file creation and changes |
|
| Automatic recovery |
Automatic recovery tool (can only be restored by the provided recovery tool) Restore by selecting the original file path or a specified new path |
|
| Motoring & Managing |
Monitoring of the backup status for individual users from the trueEP Manager Backup policies can be set for individual users from the trueEP Manager |
|
| Backup to external storage | Supporting the external backup by FTP / NAS | |
| DB backup | Supporting the Date Base backup |
Introduction of Anomaly monitoring functions
| Functions | Description |
|---|---|
| PC uptime monitoring | Signs of abnormal operation can be detected by monitoring PC uptime |
| Web page access history monitoring | Anomalies can be detected by monitoring web page access records |
| Resource usage monitoring | Anomalies can be detected by monitoring CPU, memory, network usage, etc. |
| Program installation status monitoring | Signs of malicious code installation can be detected by monitoring program installation status |
| Personal information monitoring | Prepare for personal information security by monitoring the holding status of documents containing personal information |
Differentiation of unknown attack defense principle (Patent No. 10-0676912)
| Defense principles of conventional products | Defense principles of trueEP | |
|---|---|---|
| Defense principles |
Block signature-based malware infection. - Method to prevent COVID infection with a mask |
Malicious behavior blocking. - Method of inhibiting viral activity by autoantibodies |
| Concept | Incoming packets are checked to see if they contain known malicious codes, and if so, they are deleted. | When a process behavior occurs on the PC (or server), it is determined whether the behavior was executed by the user or not, and if the behavior was not executed by the user, it is blocked. |
| Limitations |
+ Defenseless against unknown malware + Need to patch from time to time + Increased capacity of security products |
Methods to exclude the behavior of auto-executing business programs. |
| Features | Inability to fundamentally defend against unknown cyberattacks in conventional ways. |
+ Block even unknown attacks + No frequent patching required + Program size is very small ( 5MB ) |
Delivery types of trueEP
| Applied area | Descriptions | |
|---|---|---|
| By functional | Purpose of preventing hacking attacks | If you want to defend against hacking attacks and prepare for abnormal symptoms. |
| Purpose of preventing ransomware attacks | If you want to defend against ransomware attacks and prepare for abnormal symptoms. | |
| Integrated security purpose | If you want to defend against normal hacking attacks and ransomware attacks, and prepare for abnormal symptoms. | |
| By purpose | Server protection purpose | If the target to be protected are business server products. |
| PC protection purpose | If the target to be protected are business PCs. | |
| Purpose of protecting special equipments | If the target to be protected are special devices such as POS, ATM, KIOSK, Smart factory devices, etc. | |
| By service | On-premise | If you want to operate a own management server. |
| SaaS / Cloud | If you want to install only the agent and connect to the cloud-based management server for operation. |
Configurations of trueEP
Major references
Public
- President's Office
- National Assembly
- Constitutional Court
- Election Commission
- Ministry of Strategy and Finance
- Ministry of Land, Infrastructure and Transport
- Ministry of Employment and Labor
- Ministry of Health and Welfare
- Ministry of Unification
- Fair Trade Commission
- Ministry of Justice
- National Police Agency
- Seoul Metropolitan Council
- Seoul Eunpyeong-gu Office
- Gyeonggi-do Bucheon City
- Gangwon-do Hongcheon-gun Office
- Gangwon-do Taebaek City
- Daejeon Daedeok-gu Office
- Daejeon Seo-gu Office
- Daegu Dalseo-gu Office
- Daegu Waterworks Headquarters
- Gyeongnam Geoje City
- Gyeongnam Hadong-gun Office
- Jeonam Damyang-gun Office
- Jeonnam Jangheung-gun Office
- Jeonnam Gangjin-gun Office
- Gwangju Seo-gu Office
- Gwangju Dong-gu Office
- Jeonbuk Fire Headquarters
- NIPA
- KLFA
- Chungbuk Office of Education
- Social Security Information Service
- KDHC
- Korea Rail Network Authority
- Korea Midland Power
- Suwon City Corporation
- Korea Institute of Electronics Technology
- Korea Sports Association for the Disabled
Financial
- Busan Bank
- Jeonbuk Bank
- KOSCOM
- KAT
- Hanwha General Insurance
- TAM
- Acuon capital
Enterprises
- LGCNS
- Korea circuit
- BHI
- DaeA TI
- Seoul Expressway
- MH&CO
- Gallup Korea
- Daekyung tech
- Donga plating
- Dongbo
- Beyond Bio
- Sejong telecom
- SCG
- HMM Oceans
- Worldex
- Incheon Smart City
Health Care•EDU
- Kangwon National University Hospital
- Eulji University Hospital
- Gangdong Kyunghee University Hospital
- Dongsuwon Hospital
- Anyangseam Hospital
- Seoul National University of Science and Technology
- Baptist Theological Seminary
- Daejeon Health Institute of Technology
- Korea National University of Cultural Heritage
- Andong National University
- Pai Chai University
- Woosong University
- Kyungnam University
- Korean Artist Welfare Foundation
- Dongkang Medical Center
- Cultural Corps of Korean Buddhism
Special
- Lotte Mart POS
- Cheongju Commerce and Industry Security Control
- Fuji Electric(Japan)
Cloud users
In use by more than 1200 institutions by the end of 2022